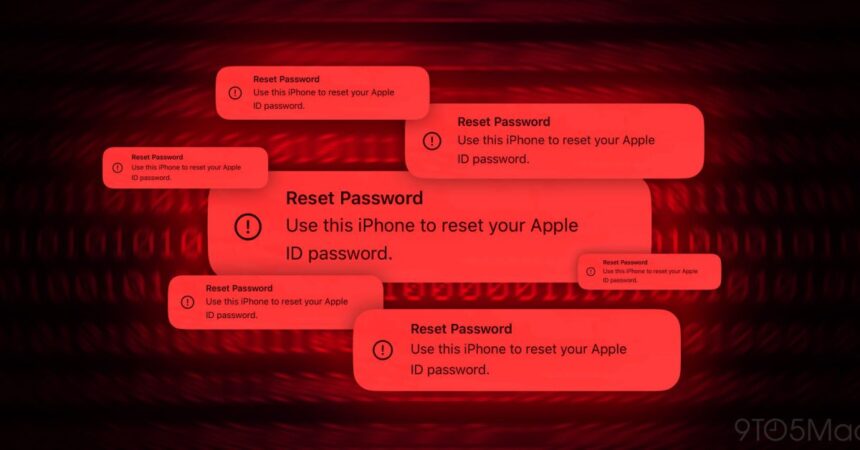
In one of the latest attacks on the iPhone, malicious parties abuse Apple‘s ID password reset system to flood users with iOS prompts to take over their accounts. Here’s how you can protect yourself against iPhone password reset attacks (often called “MFA bombing”).
We’ve recently heard of Apple users who have been subject to MFA bombing (also called MFA fatigue or push bombing). It’s not a new attack, but it can be a convincing scam, sending victims official iOS password reset messages.
As detailed by Krebs on Security (via Parth Patel), attackers who abuse this vulnerability appear to do so via an Apple user’s phone number which can bombard their iPhone and other Apple devices with over 100 system messages. MFA (Multi-Factor Authentication) to reset. your Apple ID password.
Update 04/21/24: We haven’t seen any more cases of this attack being “bombed” since Apple pushed a fix in late March. However, a Keynote USA teammate and I saw the password attack this weekend on our Apple devices.
In my case, I received the password reset message on my iPhone and my Mac. Fortunately, it was only one message on each device, so they rejected it quickly. Meanwhile, my colleague Bradley scored five.
Stay alert and safe!
Update 03/28/24 2:40 pm (Pacific Time): Keynote USA has heard from an Apple spokesperson about this issue. The company is aware of the few recent cases of these phishing attacks and Apple has taken steps to address the issue.
How to Protect Against iPhone Password Reset Attacks
- Decline, decline, decline
- Because password reset requests are a system-level alert, it seems compelling, but be sure to choose “Do not allow” for all of them
- One way attackers wear down victims is by bombarding them with hundreds of messages, sometimes over several days; keep choosing “Do not allow” and optionally use step 3 below
- Note: If you see a password reset message on the web that may be a different phishing scam, close the page since any of the buttons could lead to a malicious link
- Don’t answer phone calls – even if the caller ID says “Apple Support” or similar
- Attackers use call spoofing, which can make the incoming number appear as Apple’s official support phone number and can verify personal information, making the scam appear legitimate.
- Then they try to get a one-time passcode to take over your Apple account.
- If in doubt, decline the call and call Apple again (800.275.2273 in the US). Call spoofing should not be able to intercept your outgoing call to the real Apple.
- Apple highlights it I won’t do outgoing calls “unless the customer requests to be contacted” and that you must never share single-use codes with anyone
- Temporarily change your phone number associated with your Apple ID
- If you continue to receive messages, changing your phone number linked to your Apple ID should stop them.
- However, please note this will interfere with iMessage and FaceTime
More details
As noted in the Krebs on Security article, there appears to be a rate limit issue with the Apple ID password reset system.
What sensibly designed authentication system would send dozens of password change requests in the span of a few moments, when the user hasn’t even acted on the first few requests? Could this be the result of a bug in Apple’s systems?
Hopefully, Apple is working on a solution so that malicious parties cannot abuse this system. But unfortunately, the password reset scam has been highlighted by users for at least two years (probably more).
A recent victim shared that a senior Apple engineer advised him to turn on the recovery key feature for his Apple ID to stop password reset notifications. However, in additional testing, that was not the case, and Krebs on Security verified that Apple’s recovery key does not prevent you from being prompted to reset your password.
Keynote USA News
For Latest Apple News. Follow @Keynote USA News on Twitter Or Google News.